What is firewall?
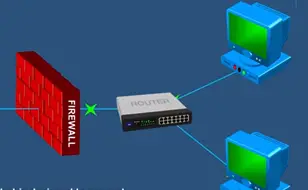
Firewall is nothing but a internet protective system which is designed to protect the private network from unauthorized access in the internet such as hacking, breaching the data base, injecting malware etc. Firewall blocks unwanted harmful traffic and permits allowed traffic.
Firewall creates a safety line between the browser and a private network. Over the internet there is hackers and malware traffic tried to penetrate into private network to cause on. Firewall is the main component on network to prevent this.
Why Firewall is Required:
It is especially important to large organisation that has lot of computer and servers. We don’t want all those devices accessible to everyone on the internet. Hackers comes by single device, then they may disturb it to whole organisation; that’s why we need firewall to protect them.
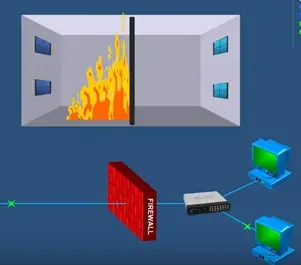
Firewall is used in computer network it works as a building structure. This Fire building structure provides a barrier when a fire is injecting from the internet refer the above picture.
Firewall is there to secure destroying entire building. If firewall is not there fire spreads over the other side and whole building will be destroyed. The same as the firewall works as a building structure.
Firewall stops harm full activities before it spreads into other side of firewall and cause harm to private network. Today hi-tech world firewall is very essential to every computer.
Especially in business organisation to keep their network safe, firewall works by filtering income data and it determines by a rows if allow to enter a network administrator. Administrator decides not only enter network but also what can leave the network.
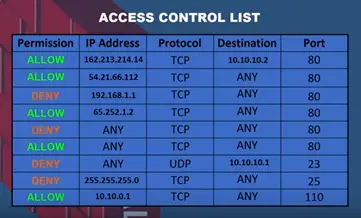
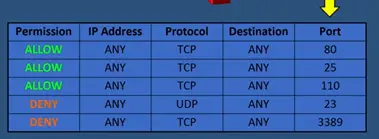
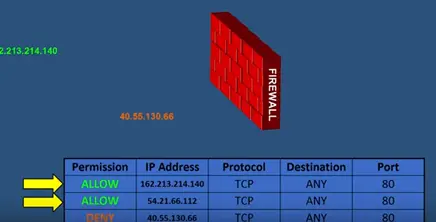
This row allows or denies the permission. For example here we show rows and firewall access control list it shows list of IP address that have been allowed or denied by this firewall.
You can see traffic from IP address allowed to enter this network from the deny IP address try to enter into network other IP firewall other IP address are granted access because the rows allow them.
Firewall makes the rows based on the IP address but also based on domain names, protocols, programs, ports and keywords. The firewall rows controlling access by port numbers.
Lest say the rows have allowed incoming data that port number 80, 25, and 110. Any incoming data using those ports can pass through the firewall. Also in the firewall rows can derived any data that using port numbers 23, 3389. If any incoming data using those port numbers, then the firewall will deny the access and won’t get pass the firewall.
Types of Firewall
There are two types of firewall. They are
- Host based firewall
- Network based firewall
Host based firewall:
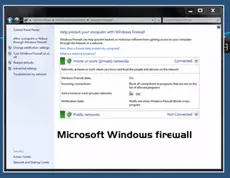
This is a software firewall. This firewall installed in a computer and that protects particular computer only nothing else.
In latest version of Microsoft operating system has a complete package of host based firewall.
In host based firewall, we can purchase it from any third party firewall sellers and that can be installed in our computer. For example zone alarm. It is popular third party host based firewall alarm and also anti-virus programs built in host based firewall.
Network based firewall
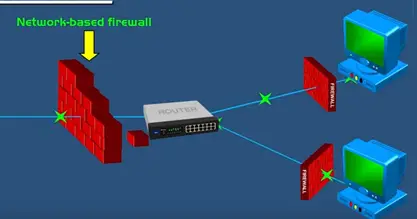
Network based firewall is a combination of hardware and software.
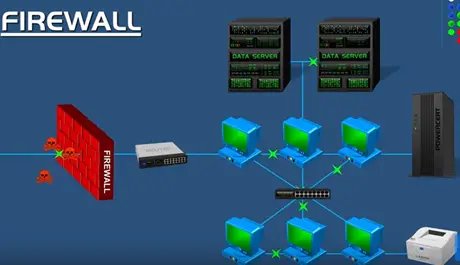
It operates on the network layer it is place between the private network and the public internet but host based network only protects the particular computer only but network based firewall protects the entire network.
It does it through management rows that are applied to entire network. So any harmful activity stopped before it reaches the computer.
Network based firewall is a standalone product which is mainly used in large organisation and also built in the component router. Which is lot of smaller organisation is realist on. They are also deployed on the server providers, cloud infrastructure lot of organisation used both network based firewall to protect network as a hole.
They also used host based firewalls for their individual protection for their computer and severs by this ensures maximum protection because harmful data get passes through network firewall the host based firewall in each computer will be there to stop it.
Image/Content Credit: https://www.youtube.com/watch?v=kDEX1HXybrU