What is OSI MODEL?
(OPEN SYSTEM INTERCONNECTION MODEL)
OSI model is defines used to understand how data is transferred from one computer to other computer in a network.
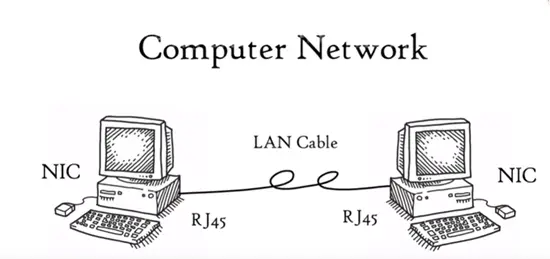
The most basic form of two computers connected each other in LAN cable and connectors sharing data with help of network interface card (NIC) forms a network. But one computer is based on Microsoft windows and other is MAC installed and how these computers are going to communicate with each other. In order to complete successful communication between computer network and different architecture the seven layer OSI model was introduced by International standard Organisation (ISO) in 1984.
The layers are
- Application layer
- Presentation layer
- Session layer
- Transport layer
- Network layer
- Data link layer
- Physical layer
Note that each layer is a package of protocols. If we say application layer it does not mean it includes computer, like chrome, Firefox etc., but it includes application layer protocol. The data need it application work correctly in a network or internet.
Application layer
The application layer is used by network. Network application means computer that use internet like google chrome, Firefox, outlook etc. Web browser is a network application running in computer. It does not reside in the application layer, but it uses application layer protocols HTTP, HTTP s to do web surfing, not only web browser but for all application including outlook, Skype etc. all are dependent on application layer protocols to function. There are dozens of application layer protocols that enables various function layers. All collectively form application layer all these protocols do file transfer, web surfing, emails, virtual terminals.
File transfer
File transfer is done with the help of FTP protocol.
Web surfing
Web surfing is done by protocol HTTP/HTTP s
Emails
Emails is used by SMTP protocol
Virtual terminals
Telnet is used for virtual terminals.
Application layer provides services for network application with the help of protocols to form user activities.
Presentation layer
Presentation layer receives data from application layer. This data is in form of characters and numbers. Presentation layer converts these characters and numbers to machine understandable format (10010) for example conversion of ASCII—EBCDIC. This function presentation layer is called translation.
Before data is transmitted the presentation layer reduces number of bits that used to represent the original data. This bit reduction process called data compression and it can be loss or lossless. Data compression reduces amount of space use to store original file as the size of file is reduced it can receive destination is very less time. That is data transmission can do faster so data compression very useful in real time audio and video streaming.
To maintain integrity of data before transmission data is encrypted and encryption is enhancing security of data. Sender side data is encrypted and receiver side data decrypted SSL, secure, sockets, layers are used for the encryption and decryption. So presentation layer perform three basic functions. Translation, data compression, Encryption and decryption.
Session layer
Session layer helps setting up and managing connections enabling sending and receiving of data followed by termination of connection or session. Session layer has its own helpers called APIs or Application Programming Interfaces. NET-BIOS ( network basic input output system) example of APLs which allows system different computer allows to communicate each other.
The connection is established with server. Server performs a function called authentication. Authentication is the process called verify. Who you are? Server uses the user name and password. Once username and password matched session or connection is established your computer and server after authentication the user authorization is checked. Authorization is process used by the server to determine if you have permission to access a file if not you will get this page. Both of authentication and authorization is performed by session layer.
Session layer keeps the track files that are being downloaded.
Transport layer
This layer controls the reliability of communication to segmentation, flow control and error control.
Segmentation data
Segmentation data received from data layer is divided into small units called segments each segments contain source and port number, segment number.
Port number- helps to connect correct application.
Segment number- it helps to reassembles segments to correct order to form correct message and receiver.
Flow control
The transport layer controls the amount of data being transmitted. Consider mobile is connected to server. Suppose server can transmit data min at 100 Mbps and our mobile process data is 10 Mbps now we are downloading data from the server, but server sending data at 50 Mbps. This is greater than the mobile process. So the mobile phone with help of transport layer can tell server slowdown data transmission rate up to 10 Mbps. So no data gets closed.
Error control
Transport layer also helps in error control. Some data does not arrive destination. Transport layer request automatic repeat request to re-transmit the loss or corrupted data.
The group of bits called checksum is added to each segment by transport layer to find out received corrupted segment. The transport layer protocols are
Transmission control protocol (TCP)
User data-gram protocol (UDP)
Network layer
Transport layer passes data to network layer. Network layer works for transmission of received data segments from one computer to another located in different networks. Data units in network layer called packets.
The functions of network layer are
- Logical addressing
- Routing (IPv4 and IPv6)
- Path determination
Logical addressing
IP addressing done in network layer is called logical addressing. Every computer has a unique address in network layer assign, sender and receiver IP address to each segment to form packets. IP address is assigned for each network for reach data each destination.
Routing
Routing is a method moving data packet to source to destination and is based on logical address format of IPv4 and IPv6
Path determination
Computer is connected to a internet server in a number of ways. Choosing best possible path to delivery from source to destination is called path determination. OSPD, BGP, IS-IS is the best for path determination.
Data link layer
It receives data from the network layer. Data link layer contain IP address of sender and receiver. There are two kinds addressing.
- Logical addressing
- Physical addressing
Logical addressing
Logical addressing is done at network layer. Where sender and receiver has a IP address is assigned to each segment to form data packet.
Physical addressing
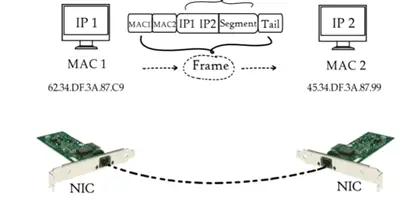
Physical layer is done at data link layer where MAC addressing of sender and receiver are assigned to each data packet form a frame. MAC address is 12 digit alpha numeric numbers embedded in network card in a computer by computer manufacturer. Data unit is data link layer called frame. Data link is embedded in software of NIC in a computer to transfer data from one computer to other by a media.
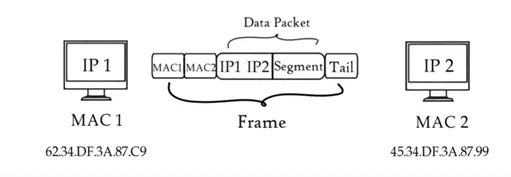
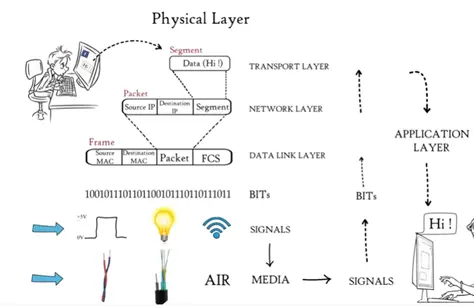
Physical layer
Till now data from application layer has been segmented by transport layer, placed into packets by network layer and framed by data link layer, which is a sequence of binary 0 and 1. Physical layer converts these binary sequence into signal and transmit over local media, it can be electrical signal is copper cable or LAN cable.
Signal generated by the physical layer is depending on types of media used to connect the receiver of physical layer receives signal covert it BITS and de-capsulated and data moves through higher layer. Finally data is moved to application layer.
Application layer protocol makes the sender message to visible in the application in the receiver computer screen.